Risk Management

Risk Management
While we want to provide you with the simplest stress-free claims process possible, we equally want to help you manage your risk and exposure.
Overview
Lost business, reputational damage and time spent dealing with a claim are just some of the hidden costs your business will face after an incident. We want to help you mitigate such risk with our proven risk management strategies and insights.
Cyber Risk Management
In a world with ever-increasing reliance on technology, cyber threats to your business continue to grow. With cybercrime annually costing more than USD$1 trillion globally and estimated to be above S$2 billion here in Singapore, cyber threats are an important and growing issue.
We’re passionate about Cyber Risk Management and helping our customers, particularly SMEs, to understand the risks associated with cyber threats. Many Cyber insurance policies only provide an insurance solution. Delta will go much further by helping you and your business adopt a robust cyber risk strategy to reduce your risk. We have partnered with a team of Asia-based cyber security experts in order to deliver a comprehensive package of services for our customers during and after any cyber incident.
Claims Handling
Delta’s cyber insurance policy covers you for a wide range of risks and our team of experts will assist you with triage, crisis and reputation management, system and data analysis and restoration, and third-party claims.
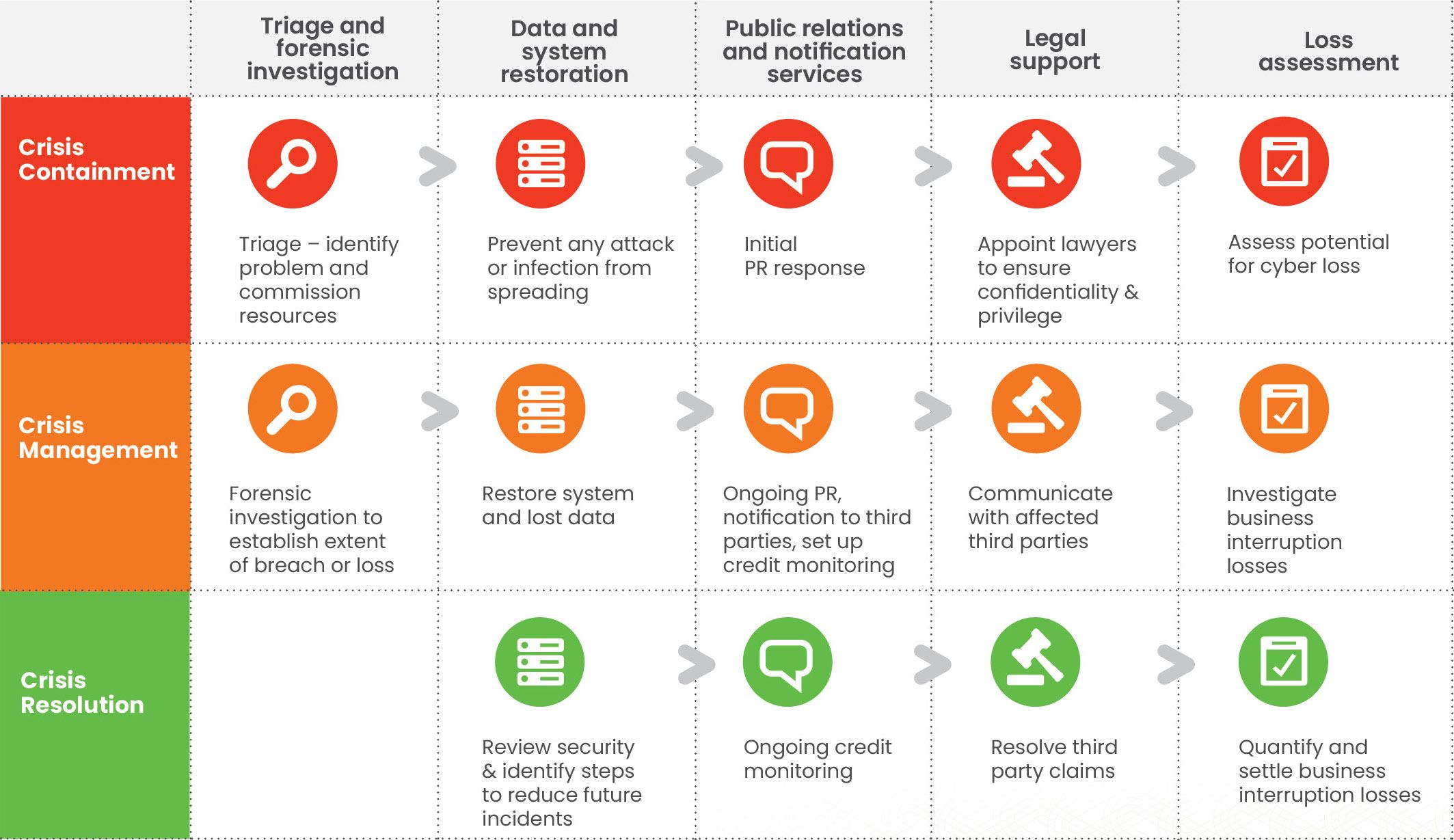
The following services are immediately available to you after a cyber attack with our Cyber Liability policy:
Business Interruption
If your IT systems are attacked, your staff may be unable to work and your customers unable to transact with you. We cover your loss of profit resulting from this.
Third Party Liability
From hacked personal information to accidentally emailing confidential information, your cyber policy covers claims by your customers and others for breaches of their privacy and the release of confidential information. It also covers social media risks, such as defamation.
Hacker Theft Cover
This provides cover where funds are stolen as a result of your network being hacked.
Public Relations Expenses
Cyber breaches hit the press every day, and urgent action may be needed to manage your reputation if it happens to you. We have specialist PR companies on hand to work with you through the crisis.
Data Forensic Services
An in-depth analysis of what has occurred, seeking 'root-cause' using investigative and forensic techniques. If required, staff can use 'chain of custody' processes to ensure the admissibility of evidence in a court of law.
Notification Services and Credit Monitoring
Many large-scale cyber attacks involve the theft of personal customer data for sale to fraudsters. We can arrange, where appropriate, for your customers to be notified and for their credit history to be monitored to prevent damage to them from identity theft.
Triage and Breach Consultation Services
When you notify a claim, we will appoint an IT specialist or a law firm, depending on the nature of the breach, to contact you to understand what is occurring and what services are needed for you to recover from the crisis. They can then manage the appointment of any additional specialists to assist.
Incident Response
The deployment of professional Incident Responders to an insured site to help coordinate and deal with the cyber security event. The focus is to contain the incident and resume business.
Mandatory breach reporting
Your policy provides cover for the reporting required in some areas (such as government and privacy) and preparing statements for media where relevant.
Post-loss Services
We don't close our file once a cyber claim has been resolved. If you've suffered a cyber incident, it may have exposed weaknesses in your cyber security or incident response plan. You might also be vulnerable to further attacks by the same cyber criminals. In the right circumstances, part of our claims response may be to assist with the cost of strengthening your cyber security and reviewing your emergency response plan.